
Future-proofing your site security with mobile credentials
Mobile credentials are increasing in demand as more businesses think about how they can future-proof their security investment. ICT has seen adoption rates of mobile credentials increase 10x in the last two years. As smartphones reach mass adoption and technologies such as Bluetooth® and NFC improve, this trend will only continue.
This is evident with the next generation of workers: a 2021 survey found that 80% of American universities and colleges are already using them or are planning on implementing them over the next few years.
The basics of mobile credentials
Mobile credentials live on your smartphone but work in the same way as the card or fob you’d use to gain entry into a building. They use NFC (near field communication) or Bluetooth® technology.
NFC vs. Bluetooth®
For ICT’s mobile credentials, NFC is available for Android phones and Bluetooth® is available with Android and iOS devices.
Both NFC and Bluetooth® use radio frequency technology to communicate between the credential and the reader. The main difference is that NFC has a much shorter read range than Bluetooth®. NFC has a range of less than 2 inches (5 cm), while Bluetooth® can be used up to nearly 33 feet away (almost 10 meters).
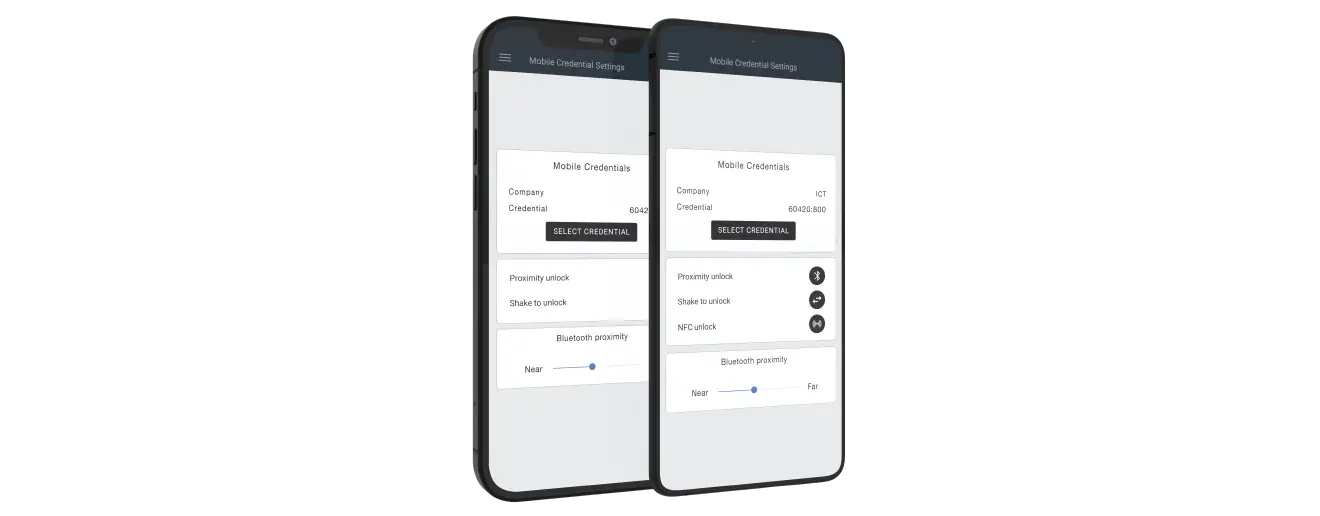
Issuing, managing, and revoking credentials: How does it work?
Credentials are issued through the Mobile Credential Portal. When you assign a mobile credential to a user, the credential will be sent to the user's email address.
Once the user accepts – AKA consumes – the credential, they will be sent to the Protege Mobile App which is where they access the credential from then on. Once a credential has been consumed, it can’t be issued to a new person or reused.
Revoking mobile credentials is easily managed through Protege WX or GX. All user credentials are stored in the user profile alongside other ICT credentials, simply click revoke and the credential will no longer be valid. Revoking a credential is like cutting up an access card – it can no longer be used. However, they can be temporarily disabled if required. So, if someone loses their phone or gets a new one, you can temporarily disable the mobile credential, remove the old device from their profile and add the new one. Simple and seamless.
Cards vs. Mobile Credentials
Mobile credential solutions have several advantages over physical access cards. Let’s explore the differences now:
Cost
According to a 2021 report by IVPM, the recurring cost of mobile credentials is cited as one the biggest barriers for access control installers and integrators getting people on board. Ongoing fees can ultimately end up costing far more than just using standard cards and fobs.
That’s why ICT doesn’t charge a subscription fee! It’s a one-time payment that costs less than many other high-frequency credential options.
Security
The security of mobile credentials is something that’s still hotly debated. There are a few things to consider when it comes to this:
Bluetooth and NFC Security
The extremely short read range of NFC makes it quite secure. To establish a connection, the smartphone must be within 2 inches (5cm) of the reader. The Bluetooth® range for the mobile credential can be adjusted in the Protege Mobile App so that the phone also needs to be close to the reader as well.
Access to the credential is authenticated using a secure cloud-based server and one of the most secure encryption methods available: AES-256.
AES (Advanced Encryption Standard) uses a cipher and matrices to substitute the data, resulting in nearly impossible to decipher combinations. In fact, 256-bit encryption has 1.1 x 1077 possible combinations, which would take a super-computer over 3 trillion years to crack. This encryption ensures added protection against card cloning and data theft, providing the highest site security.
Risk of loss
One of the greatest security risks with access cards is that they’re easily lost. A 2019 study of physical security trends in America found that 1 in 5 people had lost their access card or fob in the last year.
It may surprise you, but people Tweet when they’ve lost their access cards or fobs. You can check out the hundreds of tweets right on Twitter - you don’t even need an account.
If these losses go unnoticed or unreported, it doesn’t matter how smart the card is, it can still be used to gain access if it were to fall into the wrong hands. If you have a company logo on the card/lanyard, whoever finds it knows exactly where to go.
However, a lost phone is easily noticeable and will be reported right away. You can then immediately disable the credential through Protege WX or GX.
You’re also able to store multiple mobile credentials in the app, enabling you to select what credential you need for the site you’re visiting. No need to print and track multiple cards, meaning less stress in your day-to-day.
Multi-Factor Authentication (MFA)
If a phone is lost or stolen and someone fails to report it, your site still has many layers of multi-factor authentication protecting it.
Most smartphones are protected by MFA such as a PIN, drawing a pattern, or a biometric scan. If the malicious actor were to get past this, to access the Protege Mobile App they still need to enter another PIN. You can set how frequently you want to enter a PIN to enter the mobile app, from every time, to once a day, to every few weeks. For robust security, we recommend setting the frequency to every time or once a day.
Once you’re in the app, there is another layer of authentication: to actually send the credential you need to draw a pattern with Android or shake to unlock with iOS. Enabling these options mitigates the risk of relay attacks.
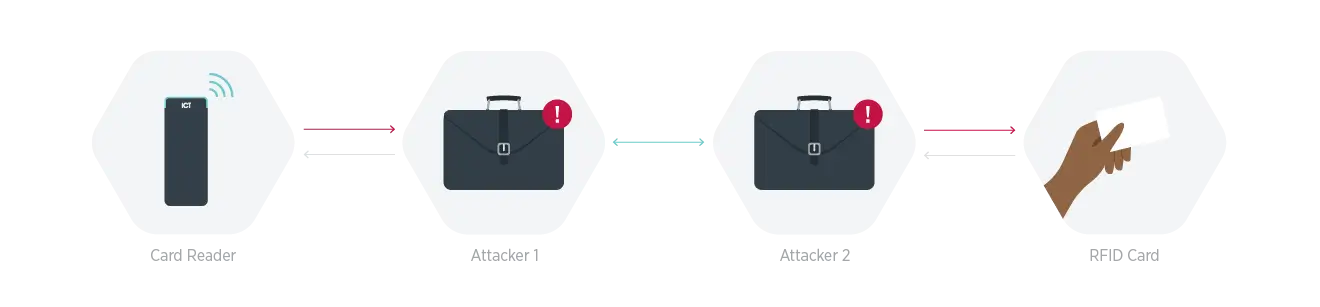
Sharing credentials
Sharing access cards is such a prevalent problem that companies spend hundreds of thousands a year to try and control this behavior. While it doesn’t seem like a big deal, it can result in people accessing areas they shouldn’t be in and lead to inaccurate reporting which could be critical in an emergency.
Additionally, low security cards pose a risk for shared facilities such as gyms, where a member could make copies for all his buddies, resulting in inaccurate reports and lost income.
However, people are very unlikely to share their phones. Sharing credentials through email or text is also mitigated because you can limit the maximum number of devices that a credential can be installed on.
Plastic waste
The environmental impacts of our decisions is something that we all must consider and try to reduce. Printing access cards only for them to be lost and printed again isn’t cost-effective or good for the Earth.
By switching from plastic access cards to mobile credentials, you can take effective steps to reduce the amount of waste going into landfills and to make your business more sustainable. That’s a win for you, your wallet, and the Earth!
Connecting to the internet and employee privacy
Privacy is something we all worry about and installing a company’s app on your phone can bring up notions of ‘big brother is always watching’. However, every time you open the Protege Mobile App, it uses the internet to check that your credential is still valid and downloads it.
The credential is not actually stored on the phone and doesn’t use any location or tracking software. The credential is simply used to identify the user, which then communicates with the reader to check whether that user ID has access rights to that area. Everyone’s privacy is secure and protected.
If the reliance on the internet is a concern, we have mitigation plans in place. The readers are still able to be used with physical access cards or fobs and one user can have up to 8 different credentials assigned to their profile.
Mobile SDK
If your business already has an app of its own, you can add ICT mobile credentials to it using our Mobile SDK (software development kit). Creating a seamless solution for your customers or tenants.
Check out our short article to learn more about our Mobile SDK solution.

Use Cases

To learn more about mobile credentials, check out the Mobile Credential product page, read the Protege Mobile Credential Management Portal User Guide, or chat with one of our knowledgeable Salespeople to help you find the solution for your needs.
Conclusion
Mobile credentials are increasing in demand for many sites. The risk of loss is mitigated and they’re inherently more secure than standard access cards and fobs. ICT’s one-time fee also means that it can be a cheaper solution as well.














