ICT offers a transitional card solution that enables a Verex operator to continue issuing credentials to new users. These dual technology cards include G-Prox™ II and MIFARE DESFire capability and are backwards compatible with legacy Verex readers and an ICT multi-technology tSec or tSec Slim Line card reader. With MIFARE DESFire onboard, you can move towards a higher security solution at your own pace.

How to mitigate the security risks of a legacy Verex system
It’s been a few years since Interlogix™ ceased production of the Verex security line in late 2019 and stopped all technical support at the end of 2021.
Since then, the security and access control landscape has continued to change, with hackers only becoming more sophisticated in their attacks.
The statistics may surprise you, but cybercrime has risen 600% since the start of the pandemic and cost US businesses over $6.9 billion in 2021 alone. If you have a small business, you may think this is not a worry for you. While often only the big attacks make the news, research shows that small businesses are 3x more likely to be targeted than large ones .


Since production of Verex ended, multiple new and high-risk attacks have been discovered. While we cannot definitively say if Verex has been affected, these are widespread industry issues.
The end of 2021 saw a major attack on Log4j. Log4j records events for errors and routine system operations and communicates diagnostic messages. For example, when you get a 404-error message on a webpage, that’s Log4j.
Hackers were able to find a way to abuse the way Log4j works to submit their own code – called Log4Shell. This opens a backdoor to not only your server, but any users communicating with that server.
Log4j is open source and widely used across the internet. Because it’s often bundled into other software, it’s difficult to trace what systems have been attacked. This type of attack is known as a software supply chain attack and in the United States, 3 out 5 companies are targeted every year. To make matters worse, because it’s such a simple attack, you don’t need to be a very skilled hacker to exploit this vulnerability.

Thankfully, many companies have built patches to ensure that their systems aren’t vulnerable. However, now production and support for Verex are no more, this is a likely vulnerability for Verex owners.
We can also look at another widely known example when in 2022, a new relay attack against Bluetooth® LE systems was found. A relay attack typically involves two people, each with a device that can pick up and copy signals from credentials like car key fobs or building credential. Person 1 stands near the victim – this can be as far as 100 meters – to pick up the signal and sends it to the second person who is standing near the Bluetooth® enabled device. This exploit allows the hacker to unlock Bluetooth® enabled devices like card readers without the credential.
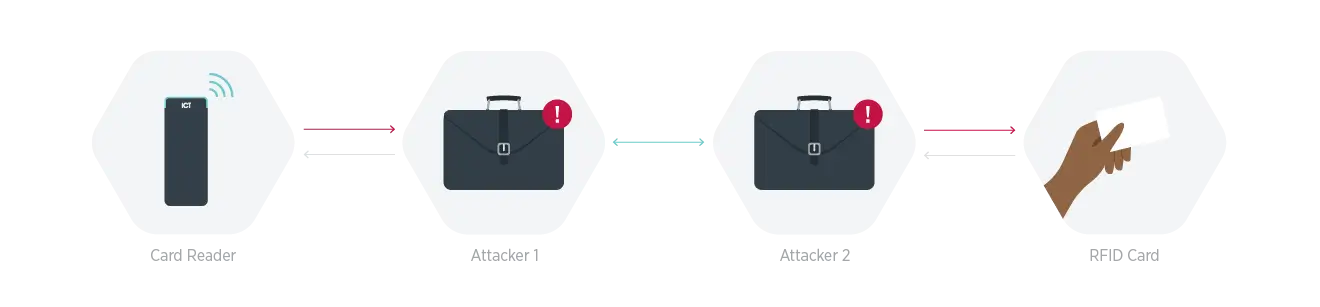
ICT has enabled several measures to ensure that your devices are secure including wave to unlock or drawing a pattern using mobile credentials. However, if your system is no longer being updated, staying on top of these trends becomes impossible. You, your people, and your business are more vulnerable to ransomware attacks, malicious actors gaining access to your system and changing settings or even creating their own credentials or PINs – no break ins or alarms going off.
A quick search on the internet is all malicious actors need to know that the Verex systems are no longer being update and are vulnerable.
Finally, if parts break, replacing them is only going to become more difficult as the years go on.
So, what can you do?
ICT has developed has 3 simple options to help your business migrate from Verex to an ICT Protege system, whether you’re a small business or a global enterprise.



ICT can cater to both SME and Enterprise requirements for legacy site migrations with either a Protege WX or Protege GX controller, all while supported Verex network modules remain in place. Expanded functionality is also enabled, however, you are limited by the constraints of the current network. Our hardware features a compact DIN rail design for convenient installation.
For a comprehensive and unified access control and intrusion solution we recommend you replace the Verex network with robust ICT hardware in addition to either Protege WX or Protege GX. When installed by an ICT Dealer Network member (IDN) all DIN Rail hardware is covered with a 5 year warranty and operators are extended peace of mind knowing the system is supported by on-call technical support and a dedicated R&D team. A full ICT migration also unlocks high security network communications, third party integrations and much more.
No need to tear out and replace your entire system, you can future-proof your business at your own pace and on your budget.
To learn more about migrating to Protege and to figure out which system is right for you, check out Key Tips when Migrating from Verex.











